In this blog, we have Dr. Jiajia Liu, the winner of the 2020 IEEE ComSoc Best YP in Academia award for the contribution to networking, communications, and security of intelligent vehicles, talking about security in Software-defined Vehicular Edge Networks.

Jiajia Liu (SM’15) is a full professor (Vice Dean) with the School of Cybersecurity, Northwestern Polytechnical University. He has published more than 190 peer-reviewed papers in many high-quality publications, including prestigious IEEE journals and conferences. He received IEEE VTS Early Career Award in 2019, IEEE ComSoc Asia-Pacific Outstanding Young Researcher Award in 2017, IEEE ComSoc Asia-Pacific Outstanding Paper Award in 2019, Niwa Yasujiro Outstanding Paper Award in 2012, the Best Paper Awards from many international conferences including IEEE flagship events, such as IEEE GLOBECOM in 2016 and 2019, IEEE WCNC in 2012 and 2014, IEEE WiMob in 2019. He was also a recipient of the Tohoku University President Award in 2013. His research interests cover a wide range of areas, including wireless and mobile ad hoc networks, intelligent and connected vehicles, and Internet of things security. He has been actively joining the society activities, like serving as associate editors for IEEE TWC, IEEE TCOM, IEEE TC and IEEE TVT, and IEEE Network and IEEE TCCN, and serving as technical program committees of numerous international conferences. He is the Vice-Chair of IEEE IOT-AHSN TC and is a Distinguished Lecturer of IEEE Communications Society and Vehicular Technology Society.
This article is based on the paper by the research group of Dr. Jiajia Liu published in IEEE Internet of Things Journal.
Let’s hear from Dr. Jiajia Liu!
Vehicular edge network
The vehicular network can promote the interaction between vehicles and the surrounding environment, realize information sharing, and improve the driving process’s safety, comfort, and efficiency. Various safety and non-safety-related vehicle services have emerged, such as road condition warnings, autonomous driving, and infotainment service. These service scenarios that have been applied or considered to have potential may be computation-intensive and delay-sensitive. At this point, edge computing becomes a promising solution. The deployment of edge servers with roadside units (RSUs) can provide the nearest computing and storage capabilities, ensuring low latency and high vehicle service performance. Besides, abstracting edge resources into virtual machines can effectively host services, further improving resource portability, utilization, and fault tolerance.
In vehicular edge network, the high mobility of vehicle nodes, the diversity of service demands, and the heterogeneity of communication technologies make network management difficult. Software-defined networking (SDN) can centralize the control logic of network devices into a controller, which can grasp network information, centrally manage RSUs and vehicles, and effectively handle network events. This way, we can significantly enhance the vehicular edge network’s flexibility, programmability, and performance.
Software-defined Networking (SDN) in vehicular edge network
SDN plays a significant role in vehicular edge network. However, most of the existing security-related works focus on using SDN to protect vehicular networks, where the controller’s global monitoring helps to realize the security policy. There is little attention to the security of SDN when applied to the vehicular network. As the brain of the software-defined vehicular edge network, the vehicular edge network may fall into global chaos when threats appear to the controller’s network state, owned by the controller.
Network topology is one of the most critical network information that the SDN controller needs to maintain. It is also relied upon by the controller and many upper-level applications to make decisions. Therefore, the correctness of network topology is essential.
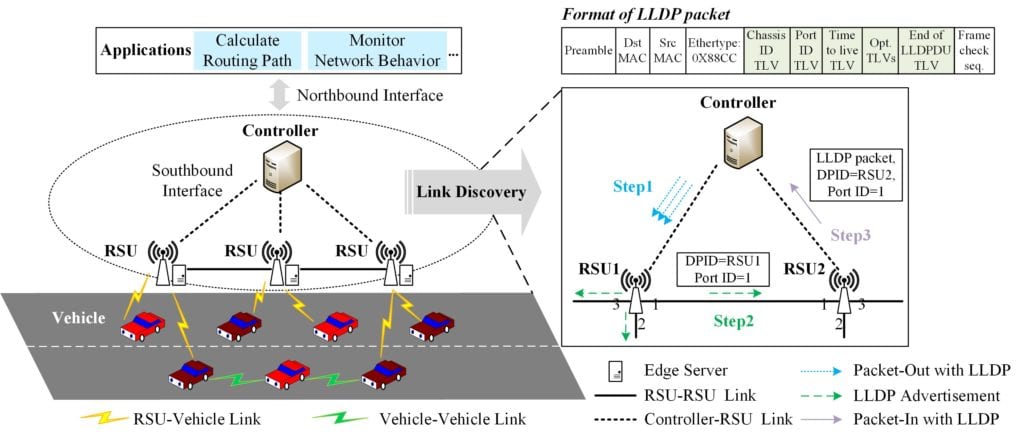
As shown in Fig. 1, the controller utilizes the link layer discovery protocol (LLDP) to discover links between RSUs. However, there are vulnerabilities in the link discovery process; that is, we cannot guarantee the integrity and source of LLDP packets and restrict the propagation of LLDP packets. Attackers can exploit these vulnerabilities to forge or relay LLDP packets, perform topology poisoning attacks, and create non-existent network connections.
Topology poisoning attacked on SDN controllers
We can emulate the software-defined vehicular edge network and implement topology poisoning attacks on SDN controllers to analyze the attack impacts from multiple aspects. A topology poisoning attack can affect routing-related applications at the application layer and lead to faulty routing path construction. At the controller layer, we see the forged network connection in the controller web console. At the infrastructure layer, this attack can affect data transmission and cause traffic fluctuation. Finally, at the vehicle layer, a man-in-the-middle attack caused by forged network connections dramatically reduces vehicle service access rates and leaks communication information.
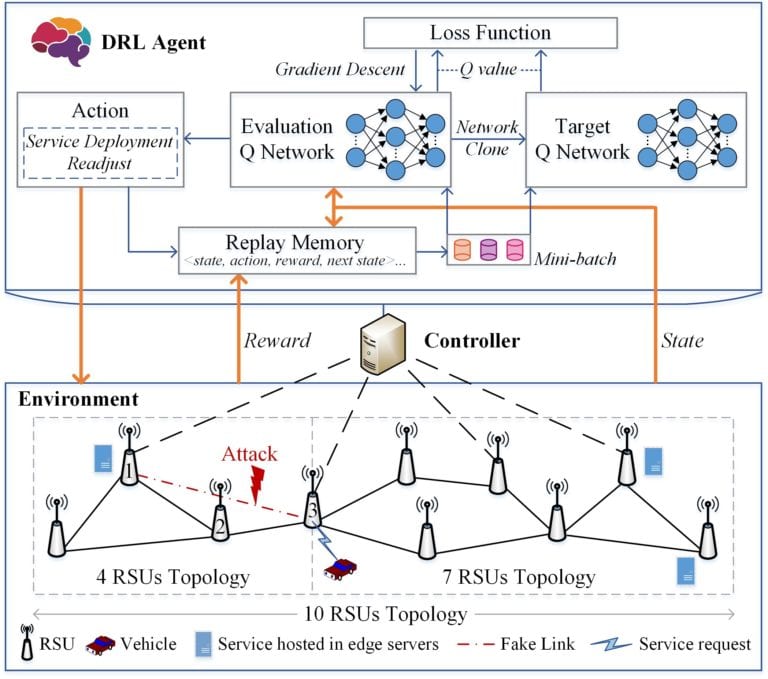
The attack tolerance scheme is critical because we cannot fully defend the topology poisoning attacks. It can cooperate with existing defense mechanisms to create time for network repair and ensure the safety and good experience of vehicle users to a certain extent. Toward this, we propose an attack tolerance scheme for topology poisoning attacks based on deep reinforcement learning (DRL). As shown in Fig. 2, with network service deployment and service access failure rate as the state, service adjustment strategy as the action, and overall service access rate as the reward, we can adaptively improve vehicles’ service access rate through the adjustment of service deployment. Thus, the vehicular edge network can have a particular self-recovery ability.
Experiments and lesson learned
We can deploy the attack tolerance module on the SDN controller. Through the southbound interface of SDN, the vehicular edge network states can be input into this module. The controller can adjust the network service deployment according to the module’s output to recover the damaged network and improve the service access rate of vehicles. Experimental results show that the software-defined vehicular edge network can operate almost normally even under the topology poisoning attack and can recover the service access rate to a near-optimal level by using this attack tolerance scheme.
In vehicular edge network, the high mobility of vehicle nodes, the diversity of service demands, and the heterogeneity of communication technologies make network management difficult. Software-defined networking (SDN) can centralize the control logic of network devices into a controller, which can grasp network information, centrally manage RSUs and vehicles, and effectively handle network events. This way, we can significantly enhance the vehicular edge network’s flexibility, programmability, and performance.
**Statements and opinions given in this blog are the expressions of the contributor(s). Responsibility for the content of published articles rests upon the contributor(s), not on the IEEE Communication Society or the IEEE Communications Society Young Professionals.
Author
Jiajia Liu, Professor, IEEE Senior Member
School of Cybersecurity, Northwestern Polytechnical University
XI AN Shaanxi 710072, China

