In this blog, Dr. Debashri Roy will discuss GAN-based learning techniques to defend against the primary user emulation attack while dynamically accessing the spectrum following her GLOBECOM 2019 paper.

Debashri is a postdoctoral fellow under the Experiential AI program at the Department of Electrical and Computer Engineering, Northeastern University, since July. She received her Ph.D. in Computer Science from the University of Central Florida in May 2020. Her research interests involve machine learning-based applications in the wireless communication domain, targeted to the areas of adversarial training, RF fingerprinting, dynamic spectrum access, beamforming and channel estimation in mmWave band, network slicing for 5G and beyond.
Debashri has received the best paper runner-up award at the IEEE IPCCC conference. She serves as a TPC member for ACM CGrid ’21, IEEE CCNC ’21, IEEE ICC ’21, ICCCN ’21. Besides, she is an associate editor in Elsevier Software Impacts journal. She has 6+ years of wireless communication research experience with more than 18 peer-reviewed publications in reputed journals and conferences. She also has 3 US provisional patents filed from her doctoral research (2018-2020) in artificial intelligence-based fingerprinting techniques in wireless communication. Her team from Northeastern University won the third prize in the beam selection track conducted by ITU for AI/ML in the 5G competition during 2020.
Let’s hear from Dr. Debashri!
Need for Spectrum Sharing
The ultra-connected world is demanding more qualitative improvement in the user experience than the earlier times. The modern world is the age of smartphones and connected IoT devices. As per the Cisco annual report (2018-2023), we will see a 15-17% surge of device usage and users from 2018 to 2023; however, we need a promise of 2x faster speed. This situation calls for the availability of more bandwidth at our expense, in both the time and frequency domain. But where can we find more bandwidth? RF spectrum is a fixed resource, so we cannot grow more spectrum as per our need. One way-out is to change the traditional spectrum management system and encourage the licensed users to share their spectrum when they are not using it; this idea is called dynamic spectrum access (DSA). The Federal Communication Commission (FCC) is already making their effort to realize the implementation of DSA in these few bands: Citizens Broadband Radio Service (CBRS), 6 GHz, TV white space. The basic idea of DSA is to allow some unlicensed users (secondary users) to opportunistically access the spectrum of the licensed users (primary users) when the spectrum is not in use. The rules strictly restrict any harmful overlap or pretentious use of spectrum by secondary users (SUs) when primary users (PUs) are present. However, the whole idea of DSA is yet to be perfected, standardized, and solidified.
Comes with the Threat: Primary User Emulation Attack
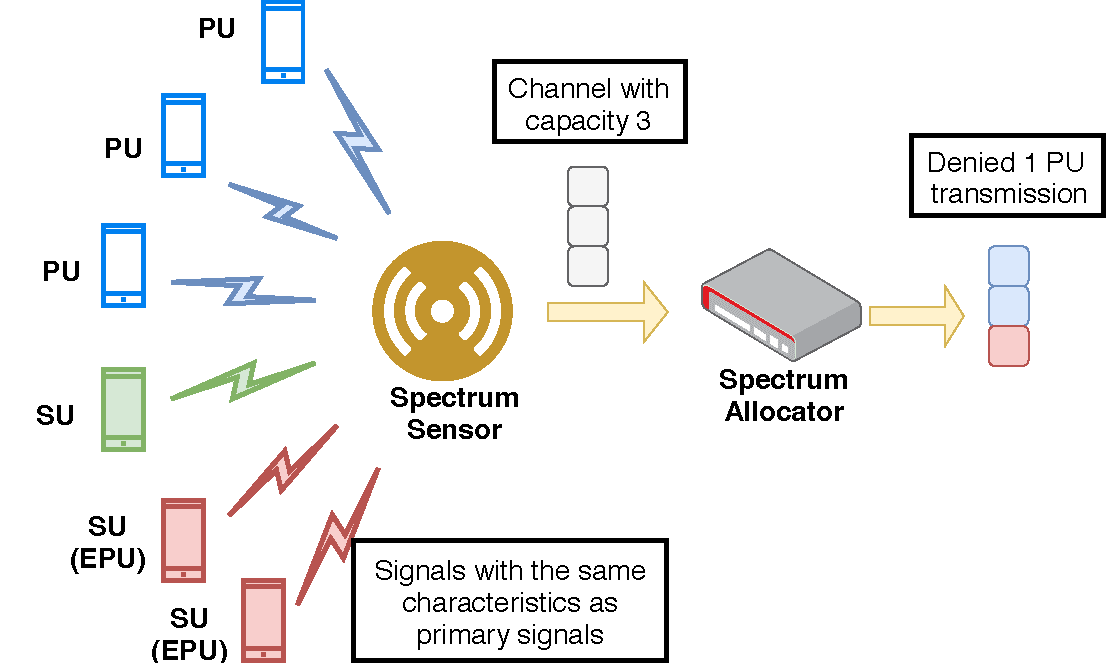
FCC mandated that all SUs must release the occupied spectral band as soon as any PU starts to transmit in that band, ensuring full privacy and availability for the licensed users. However, since the network deployments lack any measure to implement the security guidelines, a situation could arise where the PUs get denied the required spectrum due to the presence of a malicious SU. We could categorize this threat as a denial-of-service (DoS) attack. An adversarial SU could pose itself as a PU by transmitting the signal with characteristics identical to the PU. Such malicious SUs could threaten the integrity of the network deployment in two ways. First, it could preempt the existing SUs in any spectral band, posing itself as a PU, and second, it could fool the spectrum manager to deny the PU, as the malicious SU impersonates itself as a valid PU. Such malicious deployment of large scale can hijack the entire white space of any spectrum band, thus launching a “DoS” attack on the legitimate SUs and PUs. Chen et al. first described such attacks as primary user emulation (PUE) attacks.
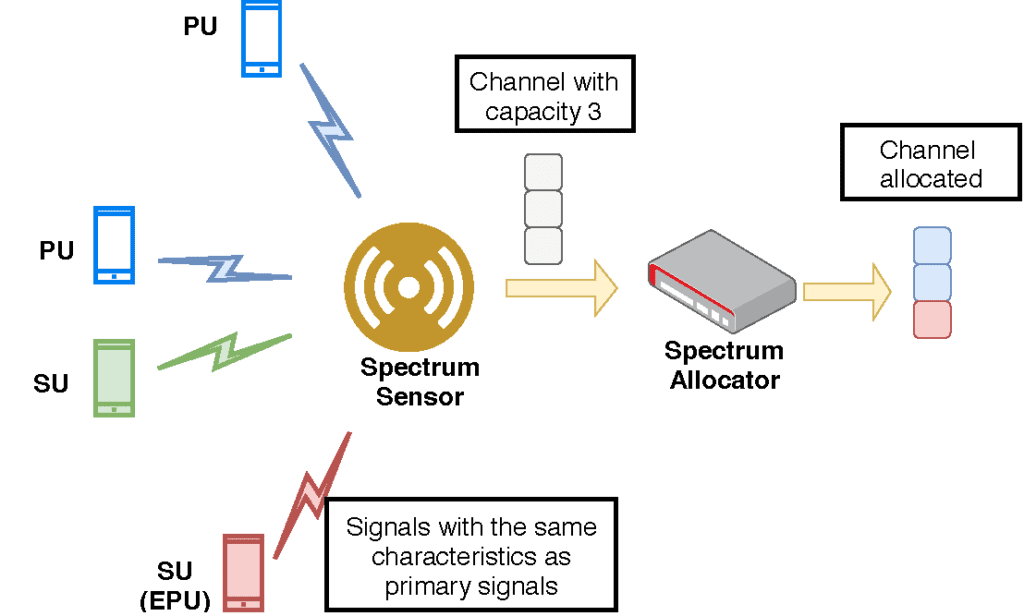
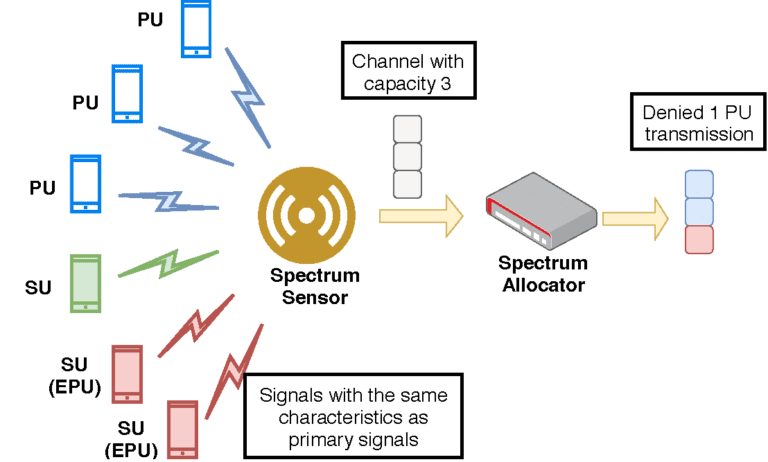
Fig. 2. An adversarial SU could pose itself as a PU by transmitting the signal with characteristics identical to the PU.
Remedy: Build an ML-based Defense Mechanism
Considering the non-deterministic nature of PUE attackers, it is nearly impossible to establish a robust defense mechanism using deterministic methods. On the other hand, wireless networks can produce a vast amount of RF data very fast. In this regard, machine learning (ML) algorithms can leverage the data’s availability to detect such nonpredictive PUE attackers. Also, ML-based methods have already proven their applicability in detecting DoS attacks in different networked systems. Therefore, we thought of proposing an ML-based framework that can build a defense system against the futuristic PUE attackers.
Why GANs?
The traditional ML algorithms mainly work by recognizing the pattern within the regulated data of the system. Even though the wireless domain has the advantage of the abundance of data, it is challenging to capture such patterns within the ever-changing wireless environment. Hence, we need to think of out-of-the-box ML approaches. One such technique is the generative adversarial net (GAN). The GAN model’s working principle is to generate and distinguish closely resembling (to the authenticated users) attackers through iterative-sequential training. In this way, the model is getting trained not only on the authenticated users but also the “yet-to-be-seen” future PUE attackers.
In a GAN, there are one generator and one discriminator. We can use two GAN-based models: (i) one model, which will work without any prior knowledge of the PU or the network environment, (ii) the other assuming that the attacker will have prior information about the PUs characteristics for that network. So, for the first case, the dumb attacker has no “prior” information (modulation schemes, geographic location, sample space, etc.) about the signal characteristics of the PUs but still tries to emulate the PUs. However, the smart attackers have sufficient information about the PU’s signal data and can emulate the PU’s signal in an intelligent way. We can also model and train two discriminators (neural networks) over the corresponding generators. Eventually, the GAN training makes the discriminator able to distinguish between a wide array of possible malicious entity types and, therefore, can detect the real adversaries with the intention of a PUE attack.
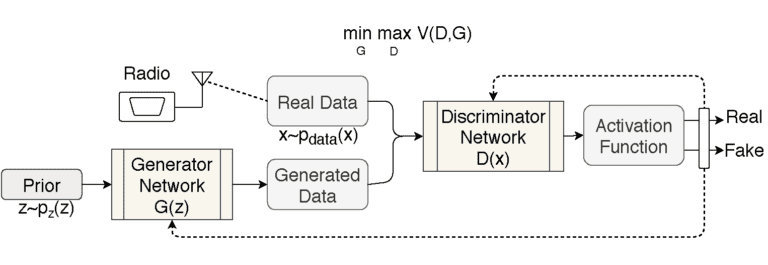
Experiments and Lessons Learned
We can deploy this model over the cognitive radio network (CRN) with the trained GAN model deployed in the centralized/distributed spectrum sensors. The idea is that the spectrum sensors will sense the spectrum, and depending on the raw data transmission, they will detect PUE attackers. It will later send this information to the spectrum allocator (to take away the allocated spectrum from the attackers) of the CRN. Our work shows that the GAN training for both kinds of generators gives a competitive accuracy for PUE attacker detection during the deployment phase through testbed evaluations. However, the GAN model with smart generator training achieves better accuracies and faster saturation than the dumb one. Besides, both models could detect malicious and selfish PUE attackers most of the time.
The ongoing advancement of DSA in the real-world communication network deployment might open up more vulnerabilities within the network and the PUE attack. However, GAN-based learning may help us be one step ahead of the adversaries by building a training mechanism that will be resilient to future attacks.
**Statements and opinions given in this blog are the expressions of the contributor(s). Responsibility for the content of published articles rests upon the contributor(s), not on the IEEE Communication Society or the IEEE Communications Society Young Professionals.