In this blog, Sabah Suhail (first in the picture) and Dr. Rasheed Hussain (second in the picture) will discuss quantum-safe hash-based signature to safeguard the internet of things ecosystem. Sabah Suhail is a Ph.D. scholar at Kyung Hee University, Korea. Her research interests include provenance, security, privacy issues in the Internet of Things, distributed ledger technology, and quantum computing. Rasheed Hussain is currently working as an Associate Professor and the Director of the Institute of Information Security and Cyber-Physical Systems at Innopolis University, Innopolis, Russia. His research interests include Information Security and Privacy, particularly security and privacy issues in Vehicular Ad Hoc NETworks (VANETs), vehicular clouds, and vehicular social networks, applied cryptography, Internet of Things, Content-Centric Networking (CCN), cloud computing, API security, and blockchain.


This blog is a short discussion of their recent work under review in a peer-review Journal. The pre-print version of this work is available here.
Let’s hear from Sabah and Dr. Hussain!
The Transition from Traditional Digital Signatures to Hash-Based Signatures
Security protocols usually rely on the cornerstone applications of digital signatures for authentication, integrity, and non-repudiation. For instance, code signing of devices for legitimate software updates, Distributed Ledger Technology to ensure valid cryptocurrency transactions, and Vehicular Ad hoc NETwork to ensure reliable message communication among vehicles or road-side units uses digital signatures.
In these real-world scenarios, the most widely used cryptographic schemes for digital signatures are RSA, DSA, and ECDSA. The security of these classical cryptographic primitives relies on the hardness of factoring integers and computing discrete logarithms. The current algorithms use large-sized cryptographic primitives that make it infeasible (and expensive) to solve discrete logarithm problem. This situation is currently valid for traditional computing systems. However, with the not-so-far arrival of quantum computers, these computational problems will be susceptible to quantum computer cryptanalysis using Shor’s algorithm. Furthermore, Grover’s algorithm can allow brute-force attacks to address quantum computing’s effect on symmetric cryptography. Therefore, the reliance on de-facto cryptographic primitives’ security is at risk of being broken by the impending quantum computers.
With the proliferation of quantum computing technologies, the epoch-making incident of the end of the currently used classical digital signature scheme in the foreseeable future raises the following concerning questions
Why are traditional signature schemes unable to withstand the quantum computers?
The exponential speed-up brought about by quantum computers stems from the fact that it acts as a massively parallel computer, which is made possible by quantum mechanics called superposition (i.e., the ability for a quantum bit (qubit) to be both a one and a zero at the same time).
What will happen if all the current cryptographic security solutions suddenly become ineffective?
The failure of classical cryptosystems may have a devastating effect on the systems. It may lead to the destruction of the security fabric that connects much of the omnipresent IoT world today and shortly.
When is such a dilemma going to happen?
The University of Waterloo experts claim a 1-in-7 chance of these cryptographic primitives getting affected by quantum attacks in 2026 and a 1-in-2 chance by 2031[1].
What to do now?
Both academia and industry are exploring quantum-safe schemes to provide security to IoT applications. They are hash-based, lattice-based, multivariate polynomial based, code-based, and super singular isogeny methods.
Among these quantum-secure signature schemes, Hash-Based Signature (HBS) schemes are well-studied schemes with minimal security requirements, practiced, reasonably fast, yield small size signatures, and have substantial security guarantees addition to other striking features summarized in Fig. 1.
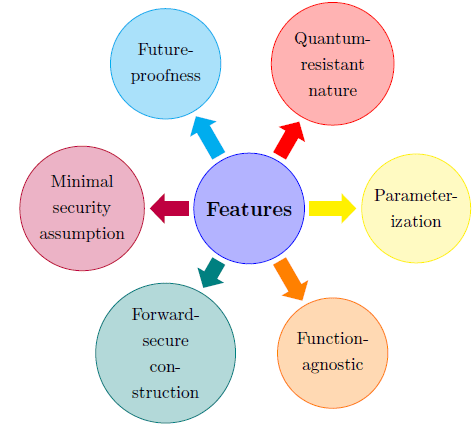
What do We need?
The following areas should be further researched or investigated.
❏ What factors should we consider to improve the data integrity of IoT devices against large-scale quantum computers that stems from multiple factors, for instance, careful selection of HBS grounds for the underlying application requirements, device constraints, and design optimization criterion?
❏ While we are still preparing for quantum-safe algorithms, at the same moment, we have to protect the information that is already vulnerable. Therefore, the overarching question is: Which defensive strategies should be adopted by the government and corporate organizations to mitigate potential liabilities?
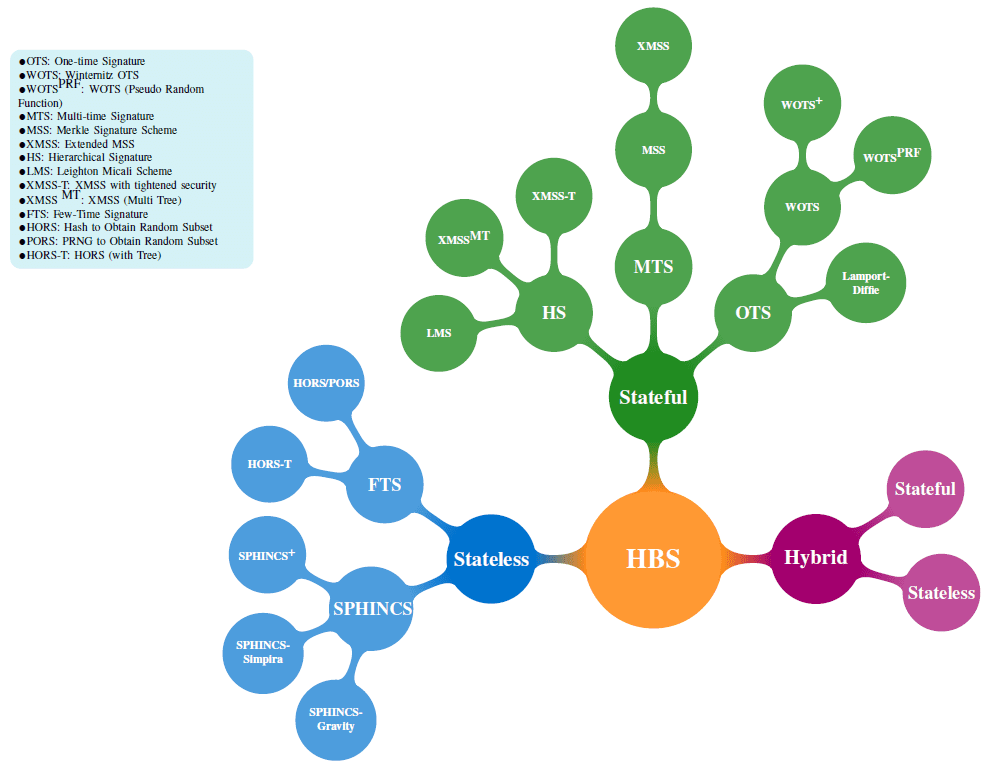
In summary, digital signatures’ security mechanisms coerce the need for rigorous scrutiny to thwart both classical and post-quantum attacks. This situation calls for state-of-the-art security solutions for resource-constrained and performance-constrained IoT devices to continue utilizing the IoT-based services in the quantum world. Therefore, the inexorable march of quantum hype entails dependable quantum-safe digital signature schemes. In this regard, HBS schemes are promising candidates, offering security proofs relative to the hash’s plausible properties and the object of leading-edge standardization efforts.
References
[1] D. Swinscow-Hall, National security in a quantum world, available at https://www.imperial.ac.uk/news/192426/national-security-quantum-world/ (August 09, 2019)
**Statements and opinions given in this blog are the expressions of the contributor(s). Responsibility for the content of published articles rests upon the contributor(s), not on the IEEE Communication Society or the IEEE Communications Society Young Professionals
Authors
Sabah Suhail
PhD Candidate, Intelligent Networking Lab, Kyung Hee University, South Korea
Postal: 1732 Deokyoungdaero, Giheung-gu, Yongin-si, Gyeonggi-do, 17104, Korea
Rasheed Hussain
Associate Professor, Innopolis University, Innopolis, Russia.
Webpage: https://sites.google.com/site/rasheedinfosec/
Contact: Innopolis University,1 Universitetskaya Str.,
Innopolis, 420500,Russia.

Pingback: Product Story Through Provenance in Supply Chain: To Blockchain or Not to Blockchain – IEEE ComSoc Young Professionals