In this blog, Sabah Suhail (first in the picture) and Dr. Rasheed Hussain (second in the picture) will discuss blockchain and provenance in supply chain. Sabah Suhail is a Ph.D. scholar at Kyung Hee University, Korea, and Rasheed Hussain is currently working as an Associate Professor and the Director of the Institute of Information Security and Cyber-Physical Systems at Innopolis University, Innopolis, Russia. You can check the authors’ earlier contributions here.


Let’s hear from Sabah and Dr. Hussain!
Electronics Supply Chain (ESC)
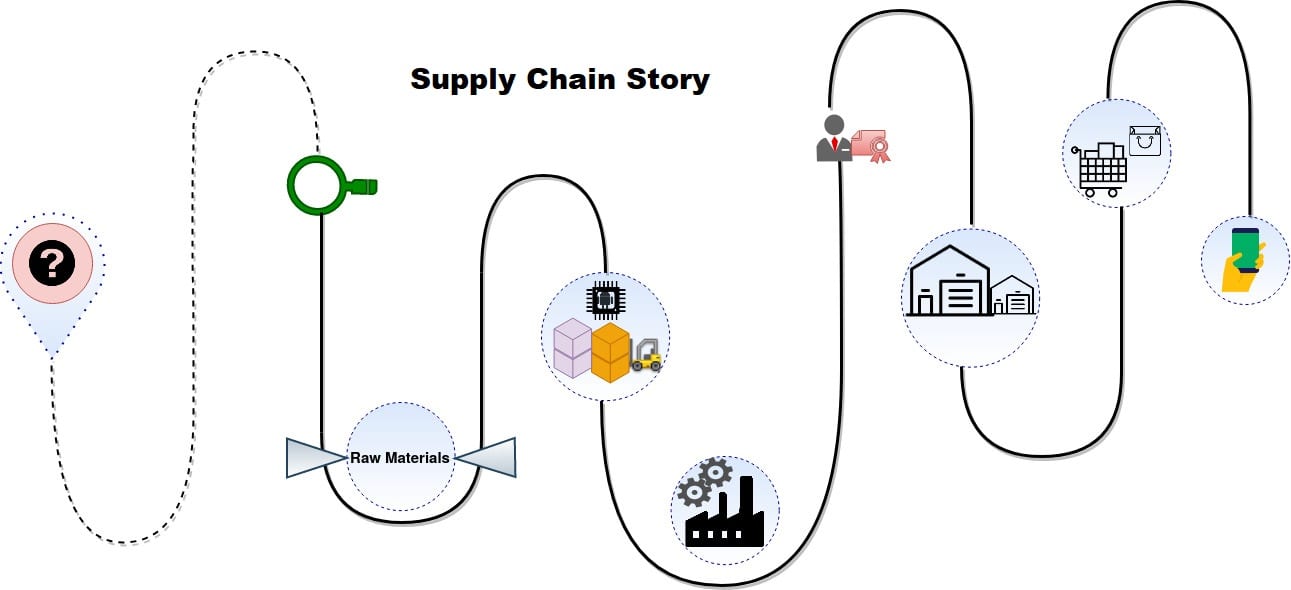
Electronics Supply Chain (ESC) revolves around an intricate process during which raw materials or natural resources get transformed into circuit boards and electronic components, integrated and assembled into end products, and ultimately made available to the customers (as illustrated in Fig. 1). Such a complex product evolution journey involving collaboration among multiple Supply Chain (SC) participating entities, each performing different operations on a product (or its parts), may raise several questions. For instance, identifying the underlying processes’ granular details (e.g., who, when, what, where, and how we derive the products).
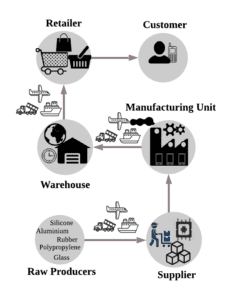
Understanding provenance in SC
To answer the questions mentioned above, SCs need a track and trace mechanism called “Provenance” to construct a complete lineage of data about products’ origin, production, modification, and custody process. Provenance in SC can enable the enterprises to choreograph their demand-supply circle, perform risk assessment, maximize revenues, investigate reasons for product recalls, and forecast their future goals. However, procuring product provenance data is an intensive task that gives rise to several other challenging issues concerning the collection, distribution, accessibility, and security of data. Therefore, due to a platform’s unavailability that can provide a one-size-fits-all solution to orchestrate a product story, it is hard to differentiate between reliable and counterfeit products. To this end, the proliferation of counterfeit products deteriorates consumer trust and causes reputational damage to its image.
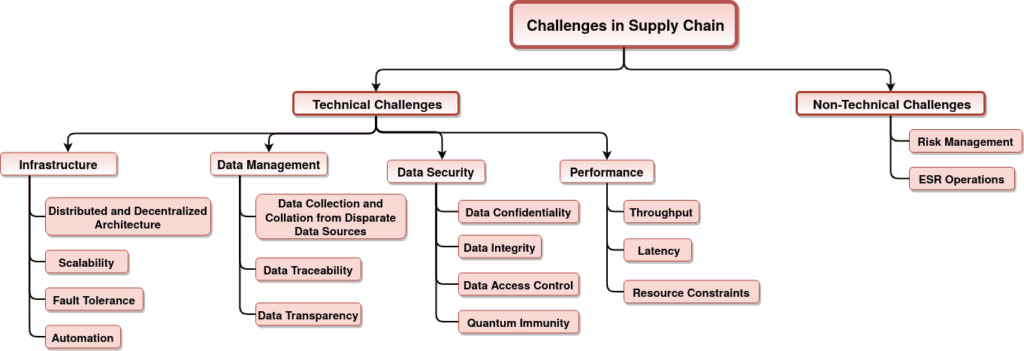
When blockchain meets SC
The imperative transition to adopt Distributed Ledger Technology (DLT) in SC received significant attention in recent years as a solution to many challenges stemming from legacy systems and privacy issues due to the multi-party access. In this regard, chain-structured blockchain’s nascent technology allows companies to record every event within SC on a ledger shared among all participants but not owned by anyone. Furthermore, this approach solves important glitches in traceability, and records events in a secure, immutable, and irrevocable way. Blockchain can provide constructive design decisions and solve many of the challenges (as shown in Fig. 2) faced by SC. However, the underlying constraints of blockchain such as “quantum-resistance” and “scalability” are overlooked by the existing solutions for SCs. Therefore, the DAG-structured DLT, for instance, IOTA, must be considered to resolve blockchain-based issues in the SC domain. IOTA exhibits quantum immune nature, provides online data accessibility, and supports fee-less microtransactions that are essential factors for future SCs.
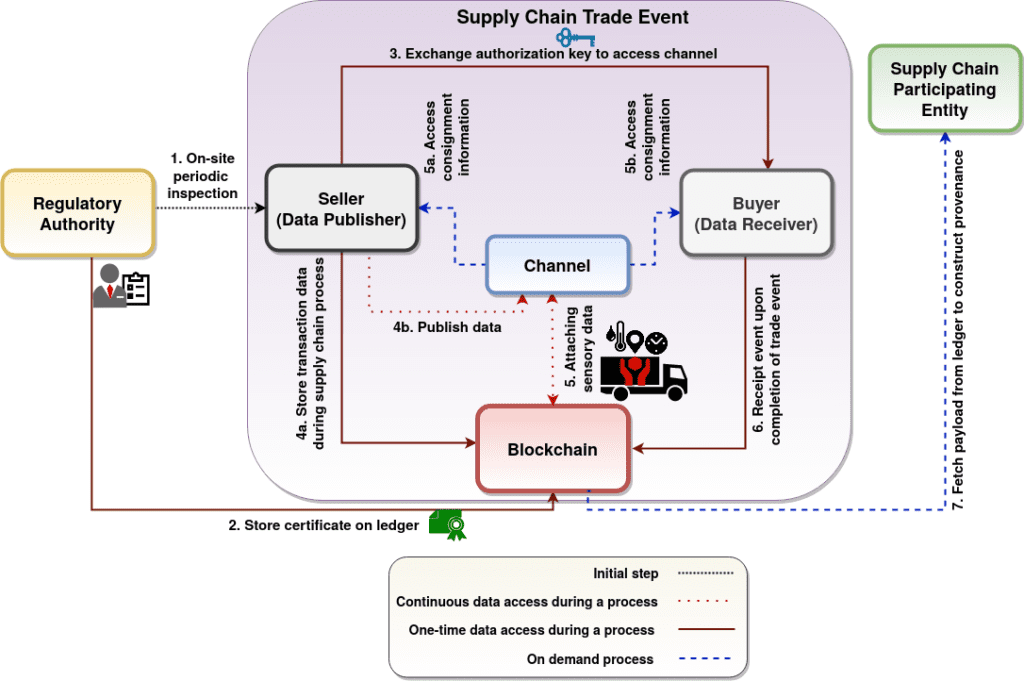
Takeaway: design principles
For a provenance-based framework for the ESC, it is of paramount importance to consider and integrate the following design principles. The first design principle is identifying the information resolution (coarse-grained or fine-grained) and data source (digital assets or humans). Comprehensive data aggregated from multiple data sources play a significant role in solving many problems such as data traceability, risk factors in trade events, operational disruptions, counterfeiting issues, etc. The second design principle is to identify erroneous data in the system to ensure “data trustworthiness” which can solve many problems such as the bullwhip effect, Garbage In Garbage Out (GIGO) problem, trust issues between a seller-buyer pair, etc. Erroneous data can be generated (either maliciously or mistakenly) by (i) source/data originator, (ii) intermediate entities, (iii) SC participating entities, and (iv) sensors or other technologies connecting the physical and digital world. The third design principle is identifying the best practices for Supply Chain Risk Management (SCRM). SCRM involves processes to identify risk events and to activate a plan accordingly to mitigate its effect. This factor covers problems such as shrinkage, outage, natural disasters, economic crisis, etc. The fourth design principle is integrating state-of-the-art technologies to automate industrial processes such as IoT, Cyber-Physical Systems (CPS), DLT, and others. The fifth design principle is evaluating non-technical factors such as Ethical, Sustainable, and Responsible (ESR) operations, i.e., labor conditions, child labor, responsible usage of natural resources (land, water, energy), etc.
**Statements and opinions given in this blog are the expressions of the contributor(s). Responsibility for the content of published articles rests upon the contributor(s), not on the IEEE Communication Society or the IEEE Communications Society Young Professionals
Authors
Sabah Suhail
PhD Candidate, Intelligent Networking Lab, Kyung Hee University, South Korea
Postal: 1732 Deokyoungdaero, Giheung-gu, Yongin-si, Gyeonggi-do, 17104, Korea
Rasheed Hussain
Associate Professor, Innopolis University, Innopolis, Russia.
Webpage: https://sites.google.com/site/rasheedinfosec/
Contact: Innopolis University,1 Universitetskaya Str.,
Innopolis, 420500,Russia.